Monday, February 25, 2013
How to effectively lose weight ith Water?
Ice cold water :
You'll burn an extra 250-to-500 calories a day
by drinking 8-to-10 glasses of ice cold water because…
Your body has to burn calories (or fat) in order to heat the ice cold water back up to your body temperature so basically…
You can lose up to 1 lb. a week JUST by drinking ice cold water.
Worm Attacks on Facebook
Your Facebook Account Can Be Hacked
Facebook currently has 4 worm (virus) Attacks.
These attacks can lead to loss of your personal information or in worse cases can get your Facebook Account Hacked
Worm 1 :- If you get a notice of a PHOTO TAG . Do not open it.
Worm 2 :- If you get a notification that a friend reported you for offensive behavior etc.. Do not open it.
Worm 3 Is a Video saying 99% of People can not watch this for more the 15 Sec. Do not open it.
Worm 4 :- All Messages from your friends via chat saying click this link .. Do not open.
All these worms are made to take your personal information and even to hack your accounts. The only way to protect yourself from these is to ignore them and not to click on them.
Now Share this info and Help your friends as well. :)
Thursday, February 21, 2013
Format and Install Operating System Using USB Flash Drive
In this tutorial you will learn, how to format and install any OS from your USB/Pendrive/memory card/Flash drive.
The method is very simple and you can use without any hassles.
Needless to say that your motherboard should support USB Boot feature to make use of the bootable USB drive.
Requirements: *USB Flash Drive (Minimum 4GB)
*Windows 7 or Vista installation files.(CD/DVD)
Follow the below steps to create bootable Windows 7/Vista USB drive using which you can install Windows 7/Vista easily.
Code that you have to execute is written in green color.
Plug-in your USB flash drive to USB port and move all the contents from USB drive to a safe location on your system.
Open Command Prompt with admin rights. Use any of the below methods to open Command Prompt with admin rights.
*Type cmd in Start menu search box and hit Ctrl+ Shift+ Enter.
Or
*Go to Start menu > All programs > Accessories, right click on Command Prompt and select Run as administrator.
You need to know about the USB drive a little bit. Type in the following commands in the command prompt:
First type
DISKPART and hit enter .
Next type
LIST DISK command and note down the Disk number (ex: Disk 1) of your USB flash drive. You may see the disk size to know about your USB.
Next type all the below commands one by one. Here I assume that your disk drive no is “Disk 1â€.If you have Disk 2 as your USB flash drive then use Disk 2.Refer the above step to confirm it. So below are the commands you need to type and execute one by one:
SELECT DISK 1
CLEAN
CREATE PARTITION PRIMARY
SELECT PARTITION 1
ACTIVE
FORMAT
(Format process may take a few minutes)
FS=NTFS
ASSIGN
EXIT
Don’t close the command prompt as we need to execute one more command at the next step. Just minimize it.
Next insert your Windows7/Vista DVD into the optical drive and check the drive letter of the DVD drive. In this guide I will assume that your DVD drive letter is “D†and USB drive letter is “H†(open my computer to know about it).
Maximize the minimized Command Prompt in the 4th step.Type the following command now:
D: CD BOOT and hit enter.
Where “D†is your DVD drive letter.
CD BOOT and hit enter again.
Type another command given below to update the USB drive with BOOTMGR compatible code.
BOOTSECT.EXE /NT60 H:
Where “H†is your USB drive letter.
Copy your Windows 7/Vista DVD contents to the USB flash drive.
Your USB drive is ready to boot and install Windows 7/Vista. Only thing you need to change the boot priority at the BIOS to USB from the HDD or CD ROM drive. I won’t explain it as it’s just the matter the changing the boot priority or enabling the USB boot option in the BIOS.
Or, You may use Novicorp wintoflash, it will do it in just few clicks, Downlaod from here, http://wintoflash.com/home/en/, run it and follow guide.
Dislike Multiple Facebook Pages Quickly
Did you like a lot of pages and want to unlike them quickly [All or few]? We have a solution for you. Just follow this tutorial to unlike the unwanted pages.
Steps:
Login to your facebook account.
Go to your profile. [See the top right side, you will see your name there, click on name to go to your profile].
You will see an option on that page, "Likes". Click on it.
Now, you will see an option there, "Edit". Click on it.
Now, scroll down a little and look up for an option, "Other Pages you like", click on it.
A box will pop-up containing your all liked page with an option "Unlike" infront of every page. Just click on "Unlike" located after that page you want to unlike.
Enjoy...
How to Hide Text Message in an Image File?
Hello friends, now i am going to teach you how you can hide text (Your message) in any image file, image file will look as normal, no measurable change of size, no damaged picture quality, no program needed, its free and happen in a few easy steps!
First open run and then type cmd, (Open cmd), now navigate the folder where you copied the files, one image file(with .jpg, .bmp, etc extensions) and one text file(which contains your message), navigate it by using this command, "cd" without "quotes".
For example, if your files are in "D" drive, then after opening cmd, type, D: and hit enter, now you are in your d drive, now if your folder name is hackalone, then, type cd hackalone and hit enter, now you are in the hackalone folder.
Do this process to locate your files.
Now, the main step, make your image file and text file ready.
Type this command after navigating your folder,
copy /b imagefilename.jpg + textfilename.txt outputimagename.jpg
Type the exact code, but dont forgot to replace the few words, imagefilename.jpg with your image file name and with proper extension, textfilename.txt with your text file, outputimagename.jpg your output image name, use whatever you want, but remember to use right extension.
All done, your message is now hidden, no one can say that the image file contains a message by looking the image, no quality loss, full gain!
But, how to view it?
Open the image with notepad, and go to last, and see the last line, your message will be at the last, read it and get protected.
Please note that, opening an image file of size 10 mb or more with notepad may freeze your system for few seconds, so keep patience.
Monday, February 18, 2013
How to Remote Shutdown your Friend's Computer?
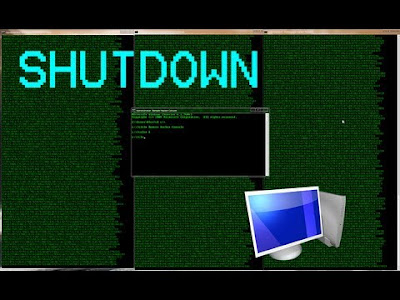
Hi there friend i will show u one cool pretty mischife with ur friends pcTongue
1)first u need to know ur friends pc name/ip-address
you can get pc name by keylogger or many software are available
or go to your friends house open his pc open his my computer right click in my computer and select properties and see his pc name
and don't forget it
2)go to start ---run---type cmd
3)in cmd type shutdown/i
4)then remote shutdown dialog box will appeare
it will look like this in pic
5)click on add button and type the pc name/ip-address of ur friend and press ok
6)and select the option u want like how u want to shutdown after how many time etc...
7)comment : comment u r friend after press ok u r friend will recive ur comment and his computer will shutdown
Enjoy :D
1)first u need to know ur friends pc name/ip-address
you can get pc name by keylogger or many software are available
or go to your friends house open his pc open his my computer right click in my computer and select properties and see his pc name
and don't forget it
2)go to start ---run---type cmd
3)in cmd type shutdown/i
4)then remote shutdown dialog box will appeare
it will look like this in pic
5)click on add button and type the pc name/ip-address of ur friend and press ok
6)and select the option u want like how u want to shutdown after how many time etc...
7)comment : comment u r friend after press ok u r friend will recive ur comment and his computer will shutdown
Enjoy :D
Saturday, February 16, 2013
Open Windows Admin Password from a Guest Account without any tool
* Go to C:/windows/system32
* Copy cmd.exe and paste it on desktop
* Rename cmd.exe to sethc.exe
* Copy the new sethc.exe to system 32,when windows asks for overwriting the file,then click yes.
When asked to overwrite,overwrite the sethc.exe
* Now log ut from your guest account and at the user select window,press shift key 5 times.
* Instead of sticky Key confirmation dialog,command prompt with full administrator privileges will open.
* Now type “ NET USER ADMINISTRATOR aaa” where “aaa” can be any password you like and press enter.
* You will see “ The command completed successfully” and then exit the command prompt and login into administrator with your new password.
* Congrats You have opened admin from guest account.
Friday, February 15, 2013
Are You Infected By Trojan?
Here are some indications that are common symptoms of getting infected with Trojan horse.
Opening and closing of CD/DVD-ROM
Computer screen blinks, turns upside down, changes resolution.
Wallpaper changes automatically.
Disable of task manager.
Task bar disappears for while.
Unusual messages.
Sudden opening of web pages.
Change in data and time of system.
Right click and left click swaps their functions.
Freezing of mouse and keyboard.
Auto movement of mouse pointer.
Playing of music even though you haven't turned on any music player.
Mouse pointer disappears.
Unusual restart and shutdown of PC.
Unwanted software installation.
Disable of Anti-Virus and Firewall.
Change in screen saver.
Disappear of task manager, tray icons, quick launch, start button and desktop icons.
Fluctuation in screen light intensity and volume.
Changing of screen savers.
Others receiving emails from you which aren't sent by you.
Rootkit Revealed
Rootkits have been associated with UNIX then Linux and today even with windows. Here in this post we will discuss tools and programs that are bundled with rootkits and their functions in short. The main job of rootkit is to provide an attacker unauthorized access to compromised system.
Once an attacker gets access to target system he/she may want to revisit system for some other malicious activities.
In general a rootkit is group of programs or tools like sniffers, keyloggers, spyware, remote administration, log cleaner, trace removers etc. Rootkit can crack the password at the admin level as well as exploit the system's vulnerability. A rootkit can compromise security of the affected system and can also violate its integrity. As mentioned earlier the main motive of rootkit is to allow repeated access of attacker to target system, installing RAT or backdoor process can serve to meet hacker this objective.
To facilitate continued access a rootkit may disable auditing and edit event log to hide its presence. Next to it, it can modify commands in UNIX and Linux system commands to make itself stealthy. It can also modify device drivers and can take over kernel even in runtime.
Now why an attacker thinks to plant a rootkit. The answer is very simple it provides undisputed and uninterrupted access, that too in super user mode, automatically sniffs important data from network, can easily hide inside command or process, can bypass nearly all security measures once installed.
The components of rootkit are installed either in user mode or in kernel mode. The user mode rootkit modifies system binaries whereas the kernel mode rootkit transforms the system calls from legitimate applications to output the attacker's data instead of the genuine data. Removal of rootkit is easy but not its payload. Rootkits can be removed using alternative drive other than which is infected or better way re-installing system.
An attacker needs administrative privileges to install rootkit in system, so its better to protect system before it gets compromised.
What are worms?
Worms are nothing but subtypes of viruses.
Unlike virus a worm doesn't require a host to replicate.
WormsWormsWorm exists in all types of virus since its only modified form of a computer virus.
can creep into another computer in network without user's assistance and hence called as worm.
Were firstly targeted towards mainframe UNIX systems but today they are very much targeted towards windows OS.
Unlike virus a worm doesn't require a host to replicate.
WormsWormsWorm exists in all types of virus since its only modified form of a computer virus.
can creep into another computer in network without user's assistance and hence called as worm.
Were firstly targeted towards mainframe UNIX systems but today they are very much targeted towards windows OS.
Learning the Java Language

What is Java?
Java allows you to play online games, chat with people around the world, calculate your mortgage interest, and view images in 3D, just to name a few. It's also integral to the intranet applications and other e-business solutions that are the foundation of corporate computing.
What is Java technology and why do I need it?
Java is a programming language and computing platform first released by Sun Microsystems in 1995. It is the underlying technology that powers state-of-the-art programs including utilities, games, and business applications. Java runs on more than 850 million personal computers worldwide, and on billions of devices worldwide, including mobile and TV devices.
Why do I need Java?
There are lots of applications and websites that won't work unless you have Java installed, and more are created every day. Java is fast, secure, and reliable. From laptops to datacenters, game consoles to scientific supercomputers, cell phones to the Internet, Java is everywhere!
Is Java free to download?
Yes, Java is free to download. Get the latest version at http://java.com/.
If you are building an embedded or consumer device and would like to include Java, please contact Oracle for more information on including Java in your device.
Why should I upgrade to the latest Java version?
The latest Java version contains important enhancements to improve performance, stability and security of the Java applications that run on your machine. Installing this free update will ensure that your Java applications continue to run safely and efficiently.
Java Download And Install Manual: http://www.java.com/en/download/help/windows_manual_download.xml
Java Tutorials: http://docs.oracle.com/javase/tutorial/java/index.html
Java allows you to play online games, chat with people around the world, calculate your mortgage interest, and view images in 3D, just to name a few. It's also integral to the intranet applications and other e-business solutions that are the foundation of corporate computing.
What is Java technology and why do I need it?
Java is a programming language and computing platform first released by Sun Microsystems in 1995. It is the underlying technology that powers state-of-the-art programs including utilities, games, and business applications. Java runs on more than 850 million personal computers worldwide, and on billions of devices worldwide, including mobile and TV devices.
Why do I need Java?
There are lots of applications and websites that won't work unless you have Java installed, and more are created every day. Java is fast, secure, and reliable. From laptops to datacenters, game consoles to scientific supercomputers, cell phones to the Internet, Java is everywhere!
Is Java free to download?
Yes, Java is free to download. Get the latest version at http://java.com/.
If you are building an embedded or consumer device and would like to include Java, please contact Oracle for more information on including Java in your device.
Why should I upgrade to the latest Java version?
The latest Java version contains important enhancements to improve performance, stability and security of the Java applications that run on your machine. Installing this free update will ensure that your Java applications continue to run safely and efficiently.
Java Download And Install Manual: http://www.java.com/en/download/help/windows_manual_download.xml
Java Tutorials: http://docs.oracle.com/javase/tutorial/java/index.html
Thursday, February 14, 2013
The Zip of Death
This is a exploit of the compression algorithms to make a small zip that will extract into extream amounts their are more ways and better ones than this one but i will only show how to make a simple 1k = 1m ratio.
1) Make a.txt file
2) Open and type the null character (alt + 255)
3) Press ctrl + a then ctrl + v a couple times to make some null bytes
4) If u have a hexeditor make the hex 00 for about 50 kilobytes.
5) Now make several copies of a.txt and name accordinly
6) Open cmd.exe
7) Type copy /b *.txt b.txt
8) Now every copy is made into a super copy and repeat
9) Once you have a nice empty big text file like 1gb. Put it in a zip archive.
Because of the simple construction of the file, 1gb of null bytes.....!
The zip is only 1 mb in size and can really annoy freinds.
For added fun hex edit the zip and you will see a bunch of hex 5555
Just add some more and the file will expand amazingly
Make sure to not open this after
You can always create your zip of death from the command line in linux
dd if=/dev/zero bs=1000 count=1000000 | gzip > test.gz
Folder Lock With Password Without Any Software
Paste the code given below in notepad and 'Save' it as batch file (with extension '.bat').
Any name will do.
Then you see a batch file. Double click on this batch file to create a folder locker.
New folder named 'Locker' would be formed at the same location.
Now bring all the files you want to hide in the 'Locker' folder. Double click on the batch file to lock the folder namely 'Locker'.
If you want to unlock your files,double click the batch file again and you would be prompted for password.
Enter the password and enjoy access to the folder.
if EXIST "Control Panel.{21EC2020-3AEA-1069-A2DD
if NOT EXIST Locker goto MDLOCKER
:CONFIRM
echo Are you sure u want to Lock the folder(Y/N)
set/p "cho=>"
if %cho%==Y goto LOCK
if %cho%==y goto LOCK
if %cho%==n goto END
if %cho%==N goto END
echo Invalid choice.
goto CONFIRM
:LOCK
ren Locker "Control Panel.{21EC2020-3AEA-1069-A2DD
attrib +h +s "Control Panel.{21EC2020-3AEA-1069-A2DD
echo Folder locked
goto End
:UNLOCK
echo Enter password to Unlock folder
set/p "pass=>"
if NOT %pass%==type your password here goto FAIL
attrib -h -s "Control Panel.{21EC2020-3AEA-1069-A2DD
ren "Control Panel.{21EC2020-3AEA-1069-A2DD
echo Folder Unlocked successfully
goto End
:FAIL
echo Invalid password
goto end
:MDLOCKER
md Locker
echo Locker created successfully
goto End
:End
Format HDD with Notepad
Write The Following In Notepad Exactly as it says
Code : 010010110001111100100101010101
Save As it as .EXE and any Name would Do.
Make an Ethical use of it. This .exe file can be really dangerous.
Wednesday, February 13, 2013
How to view saved password in Google Chrome ?
Open Google Chrome
Go to Settings (Its on the Right Corner)
Then Click on Advance Settings
Scroll Down and their will be password and forms from their click on Manage saved password.
Then list of all websites whose passwords are saved on browser will be listed.
Click on show to view those passwords
Enjoy!!
Go to Settings (Its on the Right Corner)
Then Click on Advance Settings
Scroll Down and their will be password and forms from their click on Manage saved password.
Then list of all websites whose passwords are saved on browser will be listed.
Click on show to view those passwords
Enjoy!!
Shut-down The Computer After Conveying Any Message
This one is kind of an annoying trick and if
used unknowingly can certainly cause problems (am serious).
What this trick does is, after conveying a (any) message it shuts down the computer without any confirmation. In order to create the Shutdown file, follow the below mentioned steps:
Open Notepad.
Paste the following code in it:
@echo off
msg * Its time to get some rest.
shutdown -c “Error! You have to take rest! Byeeeeee” -s
Save the file with any name but with .bat extension and close it. For eg. TakeRest.bat
NOTE :- Use this carefully. If you are playing prank then keep in mind that this may lead to loss as it shuts down the computer forcefully.
What this trick does is, after conveying a (any) message it shuts down the computer without any confirmation. In order to create the Shutdown file, follow the below mentioned steps:
Open Notepad.
Paste the following code in it:
@echo off
msg * Its time to get some rest.
shutdown -c “Error! You have to take rest! Byeeeeee” -s
Save the file with any name but with .bat extension and close it. For eg. TakeRest.bat
NOTE :- Use this carefully. If you are playing prank then keep in mind that this may lead to loss as it shuts down the computer forcefully.
Delete Recycle Bin From Windows PC
Hi... Friends..
Now You can delete Recycle Bin From Your Windows PC.
If You Suppose Remove Recycle Bin From your Desktop or delete Recycle Bin From
the Windows now you can.
I Found a New Trick For Remove the Recycle Bin By Using Registry.
Simply Follow The Below Steps:
Simply Go Registry by typing regedit in run and following path
and delete this.
HKEY_LOCAL_MACHINE\SOFTWARE\Mi
urrentVersio n\Explorer\Desktop\NameSpace\{
101B-9F08-00AA00 2F954E} and restart.
Now You can delete Recycle Bin From Your Windows PC.
If You Suppose Remove Recycle Bin From your Desktop or delete Recycle Bin From
the Windows now you can.
I Found a New Trick For Remove the Recycle Bin By Using Registry.
Simply Follow The Below Steps:
Simply Go Registry by typing regedit in run and following path
and delete this.
HKEY_LOCAL_MACHINE\SOFTWARE\Mi
urrentVersio n\Explorer\Desktop\NameSpace\{
101B-9F08-00AA00 2F954E} and restart.
Top 100 Freeware (January 2013)
100 free disk image software has a graphical
interface to install necessary software on any medium.
The collection contains only the best and most relevant programs Runet.
All programs are sorted by category, most of them Russian-speaking (some need to download from the official site in Russian language pack).
In addition, the user can customize the interface to suit your needs shells, search for files, leave notes, assign hot keys to add your program (you must copy the contents of the disk), delete unnecessary to replace the existing and much more.
List of programs:
Archivers
7-zip 9.20
Bandizip 2.0.8
Extractnow 4.7.6.0
Haozip 3.0.9002
Peazip 4.8
Safety
Avast Free Antivirus 7.0.1474
AVG 2013.0.2890
AVZ 4.39
Malwarebytes Anti-malware 1.70
Panda Cloud Antivirus 2.1
Rising Pc Doctor 6.0.4.82
Spyware Terminator 3.0.0.80
Browsers
Avant Browser 2012.197
Chrome Hybrid 26.0.1387
Firefox Hybrid 18.0.1
Maxthon 4.0.3.1000
Opera Unofficial 12.12.1707
Opera Hybrid 12.13.1734
Safari (version of 05.08.2012)
Graphics
Inkscape 0.48.4
Irfanview 4.35
Picpick 3.2.2
Webshot (version of 10.11.2012)
Xnview 1.99.6
Drive
Alcohol 52% 2.0.2.4713
Ashampoo Burning Studio 6.82.4312
Burnaware 5.5
CDBurnerXP 4.5.0.3717
Daemon Tools Lite 4.46.1.0328
DvdFab Virtual Drive 1.4.1.0
Internet
Dropbox 1.6.16
Filezilla 3.6.0.2
Netsetman 3.5.2
Networx 5.2.7
Teamviewer 8.0.16642
Thunderbird 17.0.2
Winscp 5.1.2
Download Managers
uTorrent 3.3.29010 RC1
Free Download Manager 3.9.2.1288
Orbit Downloader 4.1.1.15
Download Accelerator Plus 10.0.5.0
Download Master 5.14.2.1329
Multimedia
Adobe Flash Player 11.5.502.146
Any Video Converter 3.5.7
K-lite Codec Pack 9.7.0
MediaCoder 0.8.18.5353
Mediainfo (version of 09.02.2012)
Progdvb 6.91.3
Tagscanner 5.1.630
Vkmusic 4.45
Wavosaur 1.0.7.0
Communication
Miranda IM 0.10.9
ISendSMS (version of 05.16.2012)
ICQ 8.0.5989
Teamspeak 3.0.9.2
Skype 6.1.73.129
Office
Akelpad 4.8.1
Foxit PDF Reader 5.4.5.01241
Nitro PDF 3.1.1.3
STDU Viewer 1.6.191
Notepad + + 6.2.3
Sumatra PDF 2.2.1
Taskcoach 1.3.22
Windjview 2.0.2
Players
Aimp 3.20.1165
Foobar2000 1.2.2
Gom Player 2.1.47.5133
Kmplayer 3.5.0.77
VLC Player 2.0.5
Media Player Classic HC 1.6.6.6671
Splash Lite 1.8.1
Different
Clipdiary 3.50
Cobian Backup 11.2.0.582
Hijackthis 2.0.4
Winmend Auto Shutdown 1.3.4
Xetcom Minirun 1.2.15
System
Auslogics Registry Cleaner 2.5.0.5
Crystal Disk Info 5.3.1
Defraggler 2.12.628
Java 7.0.10
Registry Life 1.40 DC 20.12.2012
Iobit Smart Defrag 2.7.0.1165
Speccy 1.20.446
Startup Delayer (version of 09.10.2012)
Toolwiz Care 2.0.0.4200
Toolwiz Time Freeze 2.0.0.4200
Wise Registry Cleaner 7.62
Utilities
BatteryCare 0.9.12.1
HWiNFO 4.10.1820
Process Hacker 2.30
NirLauncher 1.17.12
Files and Drives
CCleaner 3.27.1900
Far Manager 3.0.3000
Free Opener 1.2.0.0
IObit Uninstaller 2.4.1.295
Multi Commander 2.8.1.1275
Recuva 1.44.778
Wipe 2013.00
Wise Data Recovery 3.19
Wise Disk Cleaner 7.74
The collection contains only the best and most relevant programs Runet.
All programs are sorted by category, most of them Russian-speaking (some need to download from the official site in Russian language pack).
In addition, the user can customize the interface to suit your needs shells, search for files, leave notes, assign hot keys to add your program (you must copy the contents of the disk), delete unnecessary to replace the existing and much more.
List of programs:
Archivers
7-zip 9.20
Bandizip 2.0.8
Extractnow 4.7.6.0
Haozip 3.0.9002
Peazip 4.8
Safety
Avast Free Antivirus 7.0.1474
AVG 2013.0.2890
AVZ 4.39
Malwarebytes Anti-malware 1.70
Panda Cloud Antivirus 2.1
Rising Pc Doctor 6.0.4.82
Spyware Terminator 3.0.0.80
Browsers
Avant Browser 2012.197
Chrome Hybrid 26.0.1387
Firefox Hybrid 18.0.1
Maxthon 4.0.3.1000
Opera Unofficial 12.12.1707
Opera Hybrid 12.13.1734
Safari (version of 05.08.2012)
Graphics
Inkscape 0.48.4
Irfanview 4.35
Picpick 3.2.2
Webshot (version of 10.11.2012)
Xnview 1.99.6
Drive
Alcohol 52% 2.0.2.4713
Ashampoo Burning Studio 6.82.4312
Burnaware 5.5
CDBurnerXP 4.5.0.3717
Daemon Tools Lite 4.46.1.0328
DvdFab Virtual Drive 1.4.1.0
Internet
Dropbox 1.6.16
Filezilla 3.6.0.2
Netsetman 3.5.2
Networx 5.2.7
Teamviewer 8.0.16642
Thunderbird 17.0.2
Winscp 5.1.2
Download Managers
uTorrent 3.3.29010 RC1
Free Download Manager 3.9.2.1288
Orbit Downloader 4.1.1.15
Download Accelerator Plus 10.0.5.0
Download Master 5.14.2.1329
Multimedia
Adobe Flash Player 11.5.502.146
Any Video Converter 3.5.7
K-lite Codec Pack 9.7.0
MediaCoder 0.8.18.5353
Mediainfo (version of 09.02.2012)
Progdvb 6.91.3
Tagscanner 5.1.630
Vkmusic 4.45
Wavosaur 1.0.7.0
Communication
Miranda IM 0.10.9
ISendSMS (version of 05.16.2012)
ICQ 8.0.5989
Teamspeak 3.0.9.2
Skype 6.1.73.129
Office
Akelpad 4.8.1
Foxit PDF Reader 5.4.5.01241
Nitro PDF 3.1.1.3
STDU Viewer 1.6.191
Notepad + + 6.2.3
Sumatra PDF 2.2.1
Taskcoach 1.3.22
Windjview 2.0.2
Players
Aimp 3.20.1165
Foobar2000 1.2.2
Gom Player 2.1.47.5133
Kmplayer 3.5.0.77
VLC Player 2.0.5
Media Player Classic HC 1.6.6.6671
Splash Lite 1.8.1
Different
Clipdiary 3.50
Cobian Backup 11.2.0.582
Hijackthis 2.0.4
Winmend Auto Shutdown 1.3.4
Xetcom Minirun 1.2.15
System
Auslogics Registry Cleaner 2.5.0.5
Crystal Disk Info 5.3.1
Defraggler 2.12.628
Java 7.0.10
Registry Life 1.40 DC 20.12.2012
Iobit Smart Defrag 2.7.0.1165
Speccy 1.20.446
Startup Delayer (version of 09.10.2012)
Toolwiz Care 2.0.0.4200
Toolwiz Time Freeze 2.0.0.4200
Wise Registry Cleaner 7.62
Utilities
BatteryCare 0.9.12.1
HWiNFO 4.10.1820
Process Hacker 2.30
NirLauncher 1.17.12
Files and Drives
CCleaner 3.27.1900
Far Manager 3.0.3000
Free Opener 1.2.0.0
IObit Uninstaller 2.4.1.295
Multi Commander 2.8.1.1275
Recuva 1.44.778
Wipe 2013.00
Wise Data Recovery 3.19
Wise Disk Cleaner 7.74
Tuesday, February 12, 2013
Make Personal Diary using Notepad
Do you know that you can use your Notepad as a
simple digital diary or a personal Log-Book to keep record of your
daily work instead of using boring pen and book ?
Well, if you dont know then follow the below mentioned steps to make one for yourself !
First open up the Notepad.
Then Type in .LOG (in capital letters) and press enter.
Save it with any name and close it.
Open the file again.
When you open the file again you will see the current date and time being inserted automatically after the .LOG line.
This will happen automatically every time you reopen the the notepad file.
Well, if you dont know then follow the below mentioned steps to make one for yourself !
First open up the Notepad.
Then Type in .LOG (in capital letters) and press enter.
Save it with any name and close it.
Open the file again.
When you open the file again you will see the current date and time being inserted automatically after the .LOG line.
This will happen automatically every time you reopen the the notepad file.
World Trade Center Attack Trick on Notepad
As some of you might be knowing that the flight number of the plane that had hit World Trade Centeron that dreadful day (9/11) was Q33NY. Now call this trick a coincidence or anything else but whatever it is, it does startle us. you will be definately amazed by the this trick.
First open Notepad.
Type “Q33N” (without quotes) in capital letters.
Increase the font size to 72.
Change the Font to Wingdings.
Nokia Mobile Hack
*#67# Allows you to check the number that “On Busy Calls” are diverted to
*#67705646# Removes operator logo on 3310 & 3330
*#73# Reset phone timers and game scores
*#746025625# Displays the SIM Clock status, if your phone supports this power saving feature “SIM Clock Stop Allowed”, it
means you will get the best standby time possible
*#7760# Manufactures code
*#7780# Restore factory settings
*#8110# Software version for the nokia 8110
*#92702689# (to remember *#WAR0ANTY#)
#pw+1234567890+3# Country Lock Status. (use the “*” button to obtain the “p,w” and “+” symbols)
#pw+1234567890+4# SIM Card Lock Status.(use the “*” button to obtain the “p,w” and “+” symbols)
*#147# (vodafone) this lets you know who called you last *#1471# Last call (Only vodafone)
*#21# Allows you to check the number that “All Calls” are diverted To
*#2640# Displays security code in use
*#30# Lets you see the private number
*#43# Allows you to check the “Call Waiting” status of your phone.
*#61# Allows you to check the number that “On No Reply” calls are diverted to
*#62# Allows you to check the number that “Divert If Unreachable(no service)” calls are diverted to
#pw+1234567890+3# Country Lock Status. (use the “*” button to obtain the “p,w” and “+” symbols)
#pw+1234567890+4# SIM Card Lock Status.(use the “*” button to obtain the “p,w” and “+” symbols)
*#147# (vodafone) this lets you know who called you last *#1471# Last call (Only vodafone)
*#21# Allows you to check the number that “All Calls” are diverted To
*#2640# Displays security code in use
*#30# Lets you see the private number
1 Imagine ur cell battery is very low, u r expecting an important call and u don’t have a charger.
Nokia instrument comes with a reserve battery. To activate, key is “*3370#”
Ur cell will restart with this reserve and your instrument will show a 50% increase in battery.
This reserve will get charged when u charge your cell next time.
*3370# Activate Enhanced Full Rate Codec (EFR)-Your phone uses the best sound quality but talk time is reduced by approx. 5%
#3370# Deactivate Enhanced Full Rate Codec( EFR)
*#4720# Activate Half Rate Codec – Your phone uses a lower quality sound
but you should gain approx 30% more Talk Time
*#4720# Deactivate Half Rate Codec
*#43# Allows you to check the “Call Waiting” status of your phone.
*#61# Allows you to check the number that “On No Reply” calls are diverted to
*#62# Allows you to check the number that “Divert If Unreachable(no service)” calls are diverted to
Is your Nokia mobile is Original or Not
Type *#06#
After you enter the code you will see a new code contain 15 digits:
43 4 5 6 6 1 0 6 7 8 9 4 3 5
IF the digit number Seven & Eight is 02 or 20 that mean it was Assembly on
Emirates which is very Bad quality
IF the digit number Seven & Eight is 08 or 80 that mean it's manufactured
in Germany which is not bad
IF the digit number Seven & Eight is 01 or 10 that mean it's manufactured in
Finland which is Good
IF the digit number Seven & Eight is 00 that mean it was manufactured in
original factory which is the best Mobile Quality ...
IF the digit number Seven & Eight is 13 that mean it was Assembly on
Azerbaijan which is very Bad quality and very dangerous for health!!
How to Remove Virus from your Mobile Phone
Learn how to remove virus or some unwanted thing from your mobile phone
Shit happens, or any virus has attacked your mobile, its inevitable u do something wrong,
Now what to do you simply have to format your phone.
To format the phone, press *#7370#, then enter the lock code,
which is the sec code of the phone.
NOTE: battery must be filled, else if format is disrupted by low battery, consequences will be disastrous
I heard the code *#7780# works too, pretty much the same i think. For 6600 users, to format the fone, there's an alternative way. Press and hold ♥>, <*>, and the buttons,
then power on fone, keep holding on the 3 buttons, till u come to a format screen. this method ONLY works on 6600, and need not enter the sec code. BUT sec code wun be reset to default 12345
How to Solve Battery low problem of mobile phone in urgent call
Your Mobile Battery is Very Low,
you are expecting an important call and you don't have a charger".
Nokia instrument comes with a reserve battery.
To activate the battery, the key-in *3370#
your cell will restart with this reserve and your instrument will show a 50% increase in battery.
This reserve will get charged when you charge your mobile next time.
Secret iPhone Codes
What a good day. Here are some more secret iPhone codes for you to enjoy. After realizing that the *3001#12345#* was a familiar Nokia code, I decided to spend some time googling for other phone codes that might work on the iPhone. These (mostly) do. There are more. Feel free to add your own to the comments.
*3001#12345#* and tap Call. Enter Field Mode
*#06# Displays your IMEI. No need to tap Call.
*777# and tap Call. Account balance for prepaid iPhone.
*225# and tap Call. Bill Balance. (Postpaid only)
*646# and tap Call. Check minutes. (Postpaid only)
*#21# and tap Call. Setting interrogation for call forwards.
*#30# and tap Call. Calling line presentation check.
*#76# and tap Call. Check whether the connected line presentation is enabled or not.
*#43# and tap Call. Determine if call waiting is enabled.
*#61# and tap Call. Check the number for unanswered calls.
*#62# and tap Call. Check the number for call forwarding if no service is available.
*#67# and tap Call. Check the number for call forwarding when the iPhone is busy.
*#33# and tap Call. Check for call control bars.
Tips and Tricks for Symbian mobile or for Smart Phone
Smartphones
Symbian Mobile Tricks and Tips
Tip 1: Do u know how to use the edit button (abc or pencil button)?
Hers how… in the inbox for example; u want to delete multiple sms, simply hold the edit button, scroll down, and then, press c to delete the marked sms. The edit button can also b used to copy and past text in sms, simply hold it and scroll across, choose copy. Pretty good for placing song names in ngages
Tip 2: ….happens, on a smart phone, its inevitable u do something wrong, and this calls for a format of phone. To format the phone, press *#7370#, then enter the lock code, which is the sec code of the phone. NOTE: battery must b full, else if format is disrupted by low battery, consequences will b disastrous
I heard the code *#7780# works too, pretty much the same I think.
For 6600 users, to format the phone, there’s an alternative way. Press and hold ♥>, <*>, and the buttons, then power on phone, keep holding on the 3 buttons, till u come to a format screen. This method ONLY works on 6600, and need not enter the sec code. BUT sec code will be reset to default 12345.
Tip 3: TO NGAGE USERS; did u know u can install .sis files simply using the cable given? Just plug it in, place the .sis file anywhere on e: (the mmc), not in any folders, root of e: disconnect, and then look for it in manager.
Tip 4: Save on battery and system memory being used by regularly checking the task manager which can be accessed by holding down the menu button!!
Tip 4a: Set the screen saver to a short time out period to prolong battery life.
Tip 4b: Avoid restarting the phone, or repeatedly turning it on and off. This helps increase battery life.
Tip 5: Type *#06# to display your IMEI serial number, very valuable for the unlocking your phone to other sim cards
Tip 6: Type *#0000# to view which firmware version you are running
Tip 7: If you would like to avoid being “blue jacked”, keep Bluetooth turned off, or set your phone’s visibility to hidden.
Tip 8: Don’t want to carry a watch and a phone? Set the screen saver to show date and time, then you can ditch the watch.
NOKIA Moblie Tips and Tricks
HOW TO DISPLAY THE HIDDEN SETTINGS OF NOKIA MOBILES?
Today tip is about the secret codes of nokia mobile phones
and will work on most of the latest nokia mobile sets. You can display the hidden information of mobile sets and troubleshoot the routine problems using these codes.
Follow the list of latest nokia codes list:
Code Action
*#7780# To restore the factory settings of mobile set
*#3283# To verify the set Manufacturing date
*#746025625# To stop the sim clock
*#67705646# Use to delete the operator logo
*#73# Use to reset game scores and phone timers
*#0000# Use to display the mobile software version
*#06# To display the IMEI Number of the mobile
*#92702689# To display the mobile warranty related settings
*#7760# To display the Production serial number
*#bta0# Use to display Bluetooth MAC address
*#9999# Use to display the mobile software version
*#2640# To display the mobile security code
*#7328748263373738# Apply to resets the set default security code
*#43# To verify the call waiting status
*#2820# To verify the Bluetooth information
*#7370# To format the mobile phone memory
*#delset# To delete the GPRS AND EMAIL settings
#pw+1234567890+1# To display the lock status of mobile set
#pw+1234567890+4# To display the lock status of your SIM
HIDING YOUR MOBILE /CELLPHONE NUMBER
Go to: Menu > Tools > Settings > Call > Send My Caller ID >
‘Yes’, ‘No’ or ‘Set By Network’ to follow the default settings of your home network.
It works only with very few network who provide you facility of “Private Number”
SPEED DIALING FROM SIMCARD CONTACT (not stored in mobile phonebook)
Type number followed by # then call.
Example: 1# or 2# or 21#
SECRET PRANK
Change closed caller group (settings >security settings>user groups) to 00000 and your phone will sound the message tone when you are near a radar speed trap.
Setting it to 500 will cause your phone 2 set off security alarms at shop exits.
Try this secret trick if you can handle the unexpected.
Note: This secret trick wont work with all phones Models.
THE DETECTIVE TIP (mobile spying)
Now you can spy on anyone using your cell phone. Just do the following.
Activate the “Automatic Answer” in the headset profile of your cell phone and set the ringing volume to “Mute”
Short-circuit the left middle and right pins on the bottom of the mobile phone with all connections touching each other this will activate profile “Headset”.
If you cant do this just keep your earphone connected to mobile.
Now place it under a table in a room and call it. Now you can use your phone for checking out what people are talking about in a room. Just call on your phone.
The phone receives the call without ringing and you can listen to what people are saying.
COMMUNICATE WITH YOUR NOKIA PHONE WITH NOKIA COMMUNICATION CENTER
Yet again, I have come up with a new applications recently released by Nokia Beta Labs.
Nokia Communication Center - It allows you to access all your mobile phone messages and contacts.
This application is some what like Nokia Pc Phone , or you can say more than it.
Advantages:
It replaces four Nokia PC Suite features - Nokia Phone Browser, Nokia Text Message Editor, Nokia Contacts Editor, and Nokia Multimedia Factory - with one simple application for all.
Installation Requirement: You must have Nokia PC Suite version 6.85 or later installed for running this application.
BLUEJACKING
First up, you need to know what Bluetooth is. There are lots of types of modern devices that incorporate Bluetooth as one of their many features. PDAs, mobile phones and laptops are a few of these modern devices. Bluetooth means that Bluetooth enabled devices can send things like phonebook/address book contacts, pictures & notes to other Bluetooth enabled devices wirelessly over a range of about 10 metres. So, we’ve got past the boring part. Now, using a phone with Bluetooth, you can create a phonebook contact and write a message, eg. ‘Hello, you’ve been bluejacked’, in the ‘Name’ field. Then you can search for other phones with Bluetooth and send that phonebook contact to them. On their phone, a message will popup saying “‘Hello, you’ve been bluejacked’ has just been received by Bluetooth” or something along those lines. For most ‘victims’ they will have no idea as to how the message appeared on their phone.
PICTURE VIEW TIPS
While you are viewing a picture in your phone’s gallery, press one of these shortcut keys (definitely works on 6600, not sure about other symbians)
1 - turn image anticlockwise
3 - turn image clockwise
* - toggle on/off of full screen
5 - zoom in
0 - zoom out
How To Block My Other Sim Card
This post is a SIM CARD Block Trick.
Just dial, **04*3814*7529*68243#
Note: Don't try in your SIM card.
Monday, February 11, 2013
Task Manager Tips
At first glance Task Manager looks like nothing more than a geeky way to tell you what you already know, the names of the programs running on your PC.
Explore out favorite Task Manager tricks, though, and you'll find all kinds of options for monitoring your system, detecting and resolving problems, especially in its most modern Windows Vista/Windows 7 incarnation. Here's what you need to know.
1. Browse your processes
Press Ctrl+Shift+Esc to launch Task Manager. By default the first thing you'll see is the Applications tab, but this is misleadingly named and of little much use as it just lists top-level windows. If you want to see what's actually running on your PC then click the Processes tab, click "Show processes from all users", and scroll down the list. If you don't know what a process is then right-click it and select Properties to get more information, such as the folder where it's stored, which will usually offer additional clues.
2. Troubleshoot startup problems
Windows Media Player is known to crash from time to time (you may have noticed this). Occasionally it'll crash without having any visible window, though, so you won't see there's a problem. Then, when you come to restart the program, nothing will happen because it's blocked by the crashed copy in RAM.
If you find Windows Media Player won't launch, then, fire up Task Manager, click the Processes tab and look for a WMPlayer.exe process. If you find one, and there's no window, then it's probably crashed. Right-click it in Task Manager, select End Process, and once it's shut down you should be able to start Media Player as normal.
Much the same problem can happen with other applications, so if something won't start, or is just misbehaving, then it's always a good idea to look for previous instances of the program. Don't use the "End Process" on anything unless you're 110% sure that it's safe to do so, though - terminating something system-critical can lock up or crash your PC immediately.
3. View memory use
It's often interesting to see which programs are using all your RAM. To find out, click the Processes tab, then click View > Select Columns, and ensure Memory - Working Set and Memory - Private Working Set are checked. You'll now see two estimates for your processes use of RAM.
The first, "Memory - Working Set" shows you how much physical memory is currently being taken up by each process. Some of this RAM may be shared by other processes, though (shared DLLS, for instance) so this figure tends to overestimate memory use.
The second, "Memory - Private Working Set" shows you how much physical memory this process alone is using (that is, it can't shared with anyone else). It will almost certainly consume additional RAM, though, so this figure tends to underestimate memory use. It's a little more reliable than the Working Set alone, but really you need to see both.
Now click the "Memory (Private Working Set)" column header so the largest figures are at the top. You'll immediately get a good feel for where your RAM is going, and which programs (if any) you need to close or tweak to get some of it back.
RAM HOGS: Find out which programs are hogging your RAM in seconds
4. Identify RAM-hogging services
Your list of processes should contain many called svchost.exe (if not, then you've not clicked "Show processes from all users"). This is the service host, a process that's used to run several Windows services. But what if this turns out to be grabbing large amounts of RAM? Which services might be to blame?
To find out more, right-click a particular svchost.exe and select Go To Services. Task Manager will open the Services tab and all the services managed by this particular instance of svchost.exe will be highlighted. Task Manager has no way to tell you how much each RAM each of the services are consuming individually, unfortunately, but this does at least greatly reduce your options. (And a hint: in most Windows Vista installations, ReadyBoost is by far the greatest resource-hogging service.)
5. Diagnose disk thrashing
Ever wondered exactly why your hard drive's been thrashing for ages, even though there's no-one at the PC? Click the Task Manager Processes tab, then click View > Select Columns, and check I/O Read Bytes and I/O Write Bytes. Click OK.
The new columns will show you the total amount of data read or written by a process, which applies to network activity as well as your hard drive. The busiest processes will have the largest figures, and if a process is active now then its totals will tick up as you watch.
6. Spot resource leaks
Sometimes processes grab more and more Windows resources, without ever quite getting around to releasing them. 32-bit Windows in particular has only a limited supply, and if this goes on for too long then your PC will become unreliable, then eventually lock up or crash.
Task Manager can help you spot a resource leak, though. Click the Processes tab, then click View > Select Columns, check Handles, User Objects and GDI Objects, and click OK. Now check these occasionally, along with the memory figures we mentioned earlier. Some of these may rise dramatically, on occasions - an antivirus tool will use many more handles when scanning, for instance, as they're used when accessing files - but if a particular resource figure is high, keeps rising, and never falls back to its starting point, then you may have a problem.
7. Stop a runaway process
If a particular process has gone rogue, using all your CPU time and reducing everything else to a crawl, then Task Manager may be able to help.
First, press Ctrl+Shift+Esc and wait for Task Manager to appear. If your runaway process is completely tying up the CPU then this can take a while, but if you don't want to reboot (you've an application with unsaved data, say) then be patient. We'd give it at least 10 or 15 minutes.
When Task Manager appears, look for the process consuming all your CPU time (click Processes, then click View > Select Columns and check CPU if that column isn't displayed). If you want to kill the process completely, then you could right-click it, select End Process and it'll die (most of the time).
This doesn't always work out as you expect, though. If the process is system-critical, maybe a Windows component, then terminating it may crash your system immediately (and it always introduces a risk of system instability). If you've data you need to save elsewhere then it may be better to try and slow down the rogue process, reduce its grab on your resources, so you can use other programs again and close everything down properly. Fortunately Task Manager can help here, too.
Right-click your CPU-hogging process, select Set Priority > Low, and Windows should immediately give more CPU time to just about everything else on your PC. The program will still be running, it just shouldn't interfere with other apps to the same degree, and they should be accessible again.
If there are still problems, right-click the process and select Set Affinity. This option lets you decide which CPU cores a process can use. If you clear one of these then that core will become available to other applications, which should significantly improve their performance.
Friday, February 8, 2013
Disable unwanted service in Windows 7 to speed up
Enables services that aren’t necessarily required by default. You can relieve a huge amount of system resources by disabling these services or setting them to “Manual mode”. Configuring a service to this setting means, it doesn’t start automatically, but rather only when it is required.
How to Disable services:
Access the “Start Menu“
Type in “services.msc” in the search line and press “Enter“. (Alternately you can open the “Control Panel“, locate the “Administrative Tools” icon and click on “Services“.)
Go to a service property page to set it to Automatic/Manual or Disabled. Right click on the service name and choose “Properties” to access the properties screen.
The configuration listed below lists a range of services you can disable to relieve system resources and yet it should provide a great experience for 95% of users. There should be little or no side effects to configuring your machine this way.
What you can disable:
Application Experience
Computer Browser (Disable this if you’re not joining any network)
Desktop Windows Manager Session Manager (Disable this if you don’t want the aero effects)
Diagnostic Policy Service
Distributed Link Tracking Client
IP Helper
Offline Files
Portable Device Enumerator Service
Print Spooler (Disable this if you do not have a printer)
Protected Storage
Remote Registry (Disable it for more Security)
Secondary Logon
Security Center
Server (Disable if you’re not running any network or intranet)
Tablet PC Input Service
TCP/IP NetBIOS Helper
Themes (Disable if you do not want aero and good visual appearance
Windows Error Reporting Service
Windows Media Center Service Launcher
Windows Search (Disable it if you hardly use Windows Search feature)
Windows Time (Disable this if you are not synchronizing system time with Internet time automatically)
That's it.. the above configuration will increase your operating system speed and you can experience better working experience on Windows 7.
Wednesday, February 6, 2013
My PC is So Slow?
A lot of people have complained that their PC
is running Slower, or is hanging etc issues. Some of these reasons may
help you in overcoming this issue:
Hard Disk Overload/Not Enough Disk Space:
You have loaded your hard disk with heavy softwares like Maya, Visual Basic, Converters, Lessons etc. Remove softwares which are not of your use/unnecessary Softwares. Because the more the hard disk is free, the better it will give you the result.
Empty Recycle Bin:
Deleting files from Recycle Bin (located on the desktop) will delete unnecessary data.
Virus And Malwares:
Trojan virus and malware spyware are a big cause of slow running of computer, Trojan is one of the dangerous viruses. Make sure you have Installed registered anti-virus and malware can program in order to protect your computer.
Drivers:
Make sure that the drivers are updated, little bit of chance that the issue may arise if not updated.
Clean Your PC:
Clean your PC with blower, or whatever method you use, a lot of dust and hairs can damage Air Flow. Which may cause over-heating.
Upgrade Your RAM:
Upgrading your RAM may solve the problem, as the type of Software you are using may need bigger RAM to run smoothly.
Hard Disk Overload/Not Enough Disk Space:
You have loaded your hard disk with heavy softwares like Maya, Visual Basic, Converters, Lessons etc. Remove softwares which are not of your use/unnecessary Softwares. Because the more the hard disk is free, the better it will give you the result.
Empty Recycle Bin:
Deleting files from Recycle Bin (located on the desktop) will delete unnecessary data.
Virus And Malwares:
Trojan virus and malware spyware are a big cause of slow running of computer, Trojan is one of the dangerous viruses. Make sure you have Installed registered anti-virus and malware can program in order to protect your computer.
Drivers:
Make sure that the drivers are updated, little bit of chance that the issue may arise if not updated.
Clean Your PC:
Clean your PC with blower, or whatever method you use, a lot of dust and hairs can damage Air Flow. Which may cause over-heating.
Upgrade Your RAM:
Upgrading your RAM may solve the problem, as the type of Software you are using may need bigger RAM to run smoothly.
Harmful Effects Of Laptop
Laptop,
Nowadays in my opinion, is the most vital tool and one of the convenient
devices for office user, for students, for businessman specially, for
housewives and now they are in a portable version, so becomes much
easier to handle.
But despite of its manifold benefits, there are some risk which the user needs to consider and be cautious about. Which may result in health injury, as laptop radiation gives off 20 mill Gauss.
Few Harmful Effects of Laptops are:
1- Infertility Issue For Men:
Laptop as per the name, is supposed to be kept in the lap, but Studies showed that when men place laptops in their laps while using, will affect man's sperm production organs, which may result in men infertility issue. This happens, because as described above that laptop releases 20 mil gauss radiation, which is harmful. Recommendation: Should use a desk or anything instead of putting it in the lap.
2- Back And Neck Issues:
The laptop screen and keyboard is very close to each other, which causes the user to bend forward in order to use comfortably. But the side effect is that it may cause back pain and neck pain, because of that you wouldn’t b able o use laptop for 2 to 3 days. Recommendation: Don’t use it continuously, give yourself rest after 2 hours continuous use.
3- Pregnancy Peril
Laptop radiation also effects pregnant women, The radiation may affect the baby’s development and risks mom or expectant mom’s health. Recommendation: Pregnant women may use desktop instead or should use desk while using a laptop instead putting it in the lap.
4- Fingers Twitching:
Laptop keyboard is arranged in such manner so that there is no extra space is left. They re awkwardly place, which is not comfortable as compared to desktop keyboard.
5- Eyesight Problem:
As the distance between the keyboard and the screen is too low, so there are chances that your eyesight may become weak, and you will be needing glasses in future.Recommendation: Low brightness level, and not to use laptop continuously.
But despite of its manifold benefits, there are some risk which the user needs to consider and be cautious about. Which may result in health injury, as laptop radiation gives off 20 mill Gauss.
Few Harmful Effects of Laptops are:
1- Infertility Issue For Men:
Laptop as per the name, is supposed to be kept in the lap, but Studies showed that when men place laptops in their laps while using, will affect man's sperm production organs, which may result in men infertility issue. This happens, because as described above that laptop releases 20 mil gauss radiation, which is harmful. Recommendation: Should use a desk or anything instead of putting it in the lap.
2- Back And Neck Issues:
The laptop screen and keyboard is very close to each other, which causes the user to bend forward in order to use comfortably. But the side effect is that it may cause back pain and neck pain, because of that you wouldn’t b able o use laptop for 2 to 3 days. Recommendation: Don’t use it continuously, give yourself rest after 2 hours continuous use.
3- Pregnancy Peril
Laptop radiation also effects pregnant women, The radiation may affect the baby’s development and risks mom or expectant mom’s health. Recommendation: Pregnant women may use desktop instead or should use desk while using a laptop instead putting it in the lap.
4- Fingers Twitching:
Laptop keyboard is arranged in such manner so that there is no extra space is left. They re awkwardly place, which is not comfortable as compared to desktop keyboard.
5- Eyesight Problem:
As the distance between the keyboard and the screen is too low, so there are chances that your eyesight may become weak, and you will be needing glasses in future.Recommendation: Low brightness level, and not to use laptop continuously.
Phishing Pages
Phishing Pages
According to dictionary.com the meaning of phishing pages is “to try to
obtain confidential information from internet user typically by sending
an email that looks as it is by a legitimate organization, but contains
a link that tricks the user to a fake website that replicates the real
one”
I will not talk on this topic that much, but will simply give you an example about the phishing page.
* Created By Hackers
* Using HTML, Javascript, CSS, PHP and other web languages
* Tricks you By creating Fake Web Page.
Like I remember when I got trapped via Phishing page on Facebook, there
was a link named as “Justin Beiber Kissing Selena Gomez” I was like
WOW! I should check on it, then what! I clicked on it, fake web
page asking me to re-enter email and password.
I did what they
ask, but then I notice the fake domain, it was like
facebook88.something.com, I was like Oh My God it’s a trap :P I changed
password then.
The funny thing was, that trap was made by my nearest and dearest friend and Co-Admin of this website, Sir RJ Wisler.
I know how to create phishing page, but cannot tell you, Its illegal :)
Ways to reduce The Risk Of Being Trapped:
Note: These rules are not only for Facebook, it also applies in sites like Ebay and other social network.
** Do not click on doubtful links, Like “John Cena Was Found Dead” “Etc Sex Tape” etc. etc.
** If you have clicked the link, and It is asking your personal information, check the domain name in the address Bar.
** If the domain name is correct, then Try by typing wrong information.
I think this is enough for your understanding, Thank You
Command Prompt (CMD) Color
Have you seen Command Prompt (CMD) fonts in a different color before? Like in blue, green etc.? No? Let’s try something different by just following simple steps, and see what you have never seen before…
Let's Have a Look,
Tutorial:
1) Click on Start >> Run then Type CMD
2) Command Prompt will open. 3) Here is the list of colors code; you just have to type “color 1” for blue. Simply if you want it to be light green just replace the number like “color A”.
0 = Black 8 = Gray
1 = Blue 9 = Light Blue
2 = Green A = Light Green
3 = Aqua B = Light Aqua
4 = Red C = Light Red
5 = Purple D = Light Purple
6 = Yellow E = Light Yellow
7 = White F = Bright White
Tutorial:
1) Click on Start >> Run then Type CMD
2) Command Prompt will open. 3) Here is the list of colors code; you just have to type “color 1” for blue. Simply if you want it to be light green just replace the number like “color A”.
0 = Black 8 = Gray
1 = Blue 9 = Light Blue
2 = Green A = Light Green
3 = Aqua B = Light Aqua
4 = Red C = Light Red
5 = Purple D = Light Purple
6 = Yellow E = Light Yellow
7 = White F = Bright White
Moringa
What is Moringa?
Moringa, also known as the Miracle Tree, is a multipurpose plant, as the leaves,
pods, fruits, flowers, roots and bark of the tree can be utilized. It is also referred
to as Drumstick Tree by the Britishers. In the Philippines, they are referred to as
malunggay or malungay. Others refer to moringa as horseradish tree, benzolive tree,
kelor, marango, mlonge, moonga, nébéday, saijhan, sajna or Ben oil tree.
What are the health benefits of moringa?
Scientific research confirms that these humble leaves are a powerhouse of nutritional
value. Gram for gram, moringa leaves contain: SEVEN times the vitamin C in oranges,
FOUR times the Calcium in milk, FOUR times the vitamin A in carrots, TWO times
the protein in milk and THREE times the Potassium in bananas.
There are many benefits of the moringa tree, but the health benefits are the most important. Research has shown that various parts of the moringa tree can be effective in a significant number of health concerns. Here’s a quick look at a few of them:
• Moringa is rich in Vitamin A. It contains four times more Vitamin A or beta-carotene than carrots. Hence, it is a weapon against blindness.
• It is also a rich source of Vitamin C many times more than oranges.
• Normally milk is said to be a rich source of calcium but the amount of calcium present in moringa leaves is way higher than in milk.
• The moringa leaves are said to contain two times the protein present in milk.
• Bananas are a rich source of potassium. But moringa leaves contain several times more potassium than bananas.
• Along with potassium, zinc is also found in large quantities in moringa.
• If moringa leaves were to be eaten by one and all, the world will be free of anemia as it contains three times more iron than spinach.
• With all the junk food eaten these days, many people face problems of high cholesterol. Moringa helps in balancing the cholesterol levels in the body.
• Essential Amino acids are also found in moringa.
• Moringa is also said to balance sugar levels, hence it is helpful in the fight against diabetes.
• The body's natural defense mechanism increases with the consumption of moringa in the daily diet pattern. Since it is an immunity-stimulant, it is prescribed for AIDS afflicted patients.
• Moringa leaves can be consumed to stimulate metabolism.
• It is also said to have digestive powers.
• It is a nutrition booster and is known to promote a feeling of well-being in people.
• If you are looking for non-sugar based energy, then moringa leaves is the answer. Thus, it will also help in the weight loss process.
• The cell structure of the body is stimulated by the moringa leaves.
• It is especially useful for lactating mothers. The consumption of moringa has shown dramatic increase in the quantity of breast milk.
• It is also famous for its anti-bacterial properties.
• The paste of the moringa leaves is said to beautify the skin and is hence applied by women regularly.
• It protects the liver and kidneys.
• It can also be used as a water purifier.
Moringa contains more than 90 nutrients and 46 types of antioxidants. With all the health benefits of moringa, it can easily be termed as the most nutritious plant on the face of the earth. There are no side-effects of moringa tree leaves which have been proved till date. At the same time it can be consumed by small children and adults alike. Therefore, many people have started using it in porridge, pastas, breads, etc., to reap the everlasting health benefits of the extraordinary
'moringa' Is moringa dried leaf powder more potent than fresh leaves?
When you take a delicate moringa leaf and carefully shade dry it - amazing things happen. There is significantly higher nutritional value in the moringa dried leaf, in some cases over ten times in specific nutrients when compared to fresh Moringa leaf. Many universities and independent research laboratory analyses have confirmed the higher nutritional values in the dried leaf powder. What's more amazing is gram for gram comparison of moringa to common fruits and vegetables. The nutritional values of moringa's many vitamins, minerals, amino acids, chlorophyll, and anti-aging compounds are higher than it's own fresh leaves.
Moringa, also known as the Miracle Tree, is a multipurpose plant, as the leaves,
pods, fruits, flowers, roots and bark of the tree can be utilized. It is also referred
to as Drumstick Tree by the Britishers. In the Philippines, they are referred to as
malunggay or malungay. Others refer to moringa as horseradish tree, benzolive tree,
kelor, marango, mlonge, moonga, nébéday, saijhan, sajna or Ben oil tree.
What are the health benefits of moringa?
Scientific research confirms that these humble leaves are a powerhouse of nutritional
value. Gram for gram, moringa leaves contain: SEVEN times the vitamin C in oranges,
FOUR times the Calcium in milk, FOUR times the vitamin A in carrots, TWO times
the protein in milk and THREE times the Potassium in bananas.
There are many benefits of the moringa tree, but the health benefits are the most important. Research has shown that various parts of the moringa tree can be effective in a significant number of health concerns. Here’s a quick look at a few of them:
• Moringa is rich in Vitamin A. It contains four times more Vitamin A or beta-carotene than carrots. Hence, it is a weapon against blindness.
• It is also a rich source of Vitamin C many times more than oranges.
• Normally milk is said to be a rich source of calcium but the amount of calcium present in moringa leaves is way higher than in milk.
• The moringa leaves are said to contain two times the protein present in milk.
• Bananas are a rich source of potassium. But moringa leaves contain several times more potassium than bananas.
• Along with potassium, zinc is also found in large quantities in moringa.
• If moringa leaves were to be eaten by one and all, the world will be free of anemia as it contains three times more iron than spinach.
• With all the junk food eaten these days, many people face problems of high cholesterol. Moringa helps in balancing the cholesterol levels in the body.
• Essential Amino acids are also found in moringa.
• Moringa is also said to balance sugar levels, hence it is helpful in the fight against diabetes.
• The body's natural defense mechanism increases with the consumption of moringa in the daily diet pattern. Since it is an immunity-stimulant, it is prescribed for AIDS afflicted patients.
• Moringa leaves can be consumed to stimulate metabolism.
• It is also said to have digestive powers.
• It is a nutrition booster and is known to promote a feeling of well-being in people.
• If you are looking for non-sugar based energy, then moringa leaves is the answer. Thus, it will also help in the weight loss process.
• The cell structure of the body is stimulated by the moringa leaves.
• It is especially useful for lactating mothers. The consumption of moringa has shown dramatic increase in the quantity of breast milk.
• It is also famous for its anti-bacterial properties.
• The paste of the moringa leaves is said to beautify the skin and is hence applied by women regularly.
• It protects the liver and kidneys.
• It can also be used as a water purifier.
Moringa contains more than 90 nutrients and 46 types of antioxidants. With all the health benefits of moringa, it can easily be termed as the most nutritious plant on the face of the earth. There are no side-effects of moringa tree leaves which have been proved till date. At the same time it can be consumed by small children and adults alike. Therefore, many people have started using it in porridge, pastas, breads, etc., to reap the everlasting health benefits of the extraordinary
'moringa' Is moringa dried leaf powder more potent than fresh leaves?
When you take a delicate moringa leaf and carefully shade dry it - amazing things happen. There is significantly higher nutritional value in the moringa dried leaf, in some cases over ten times in specific nutrients when compared to fresh Moringa leaf. Many universities and independent research laboratory analyses have confirmed the higher nutritional values in the dried leaf powder. What's more amazing is gram for gram comparison of moringa to common fruits and vegetables. The nutritional values of moringa's many vitamins, minerals, amino acids, chlorophyll, and anti-aging compounds are higher than it's own fresh leaves.
Tuesday, February 5, 2013
Monday, February 4, 2013
Friday, February 1, 2013
Subscribe to:
Comments (Atom)



























